1. Managing Remediation Plans
Overview
The Remediation Plan Module serves as a central hub for defining, tracking, and managing all remediation plans associated with identified risks, ensuring transparency, accountability, and alignment with your organisation's risk mitigation objectives.
From here, you can manage all remediation plans created during the Risk Assessment Demand process, ensuring that:
- Deficiencies in implemented controls are effectively addressed through remediation actions.
- Plans of action and milestones are developed to outline remediation steps for unacceptable risks identified during assessments.
- Security and privacy plans are updated to reflect changes resulting from implemented remediation actions.
This structured approach ensures that remediation efforts are traceable, well-documented, and aligned with your organisation's cybersecurity and risk management strategies.
Within this module, you can:
- Monitor and Review Risks: Oversee all risks registered during the Risk Assessment Demand process, ensuring each is properly tracked and addressed.
- Mark Risks as Closed: Indicate when a risk has been mitigated or is no longer applicable.
- Delete a Risk: Remove risks that are no longer relevant.
- Define Resource Owners: Assign responsibility for each risk to specific individuals or teams.
Monitor and Review Remediation Plan
Remediation Plans in the Remediation Plan Registry Module are view-only. To modify a Remediation Plan, click on the "edit button".
From there, you will be able to:
- Update the informations (Contacts, Due Date, Description and Implementation Challenges).
- Mark the Remediation Plan as Completed
- Define Resource Owners.
Mark Remediation Plan as Completed
Once all required actions are finalised and no further updates are needed, the analyst should mark the Remediation Plan as "Completed".
- Navigate to the Remediation Plan Module.
- Locate the Remediation Plan that needs to be indicated as "Completed".
- Click on the vertical dots in the card.

- Select "Mark Completed".
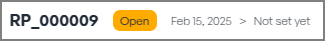
- The Risk Status changes from "Open" to "Pending Validation"
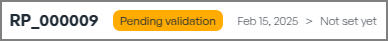
- Select "Confirm Completion".

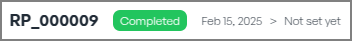
- The Risk Status changes from "Pending Validation" to "Completed".
Reopen a Remediation Plan
If reopening a Remediation Plan is necessary, follow these steps:
- Navigate to the Remediation Plan Module.
- Locate the Closed Remediation Plan that requires updates.
- Click on the vertical dots in the card.

- Select "Reopen RP".
- The Remediation Plan changes from "Completed" to "Open"

Delete a Remediation Plan
Deleting a Remediation Plan is not possible directly from the Remediation Plan Registry.
To delete a Remediation Plan, you must edit the risk in which the Remediation Plan was originally created.
Additionally, a Remediation Plan cannot be deleted if it has been marked as "Completed". If the Remediation Plan that needs to be deleted has been previously marked as "Completed", it must first be reopened before deletion is possible.
Steps to Delete a Remediation Plan
- Navigate to the Risk Registry Module.
- Locate the Remediation Plan that needs to be deleted.
- Click on the vertical dots in the card.

- Select "Delete RP".
- A confirmation prompt will appear.
On This Page
Overview
Monitor and Review Remediation Plan
Mark Remediation Plan as Completed
Reopen a Remediation Plan
Delete a Remediation Plan
Found an issue?
Report issue